Securing Remote Connection: A Comprehensive Guide for Businesses

In today's digital landscape, businesses are increasingly adopting remote work models. With this shift, the necessity for securing remote connection has never been more critical. This article delves into methods, technologies, and best practices to enhance your business's cybersecurity while ensuring efficient remote operations.
Understanding the Importance of Securing Remote Connections
The global pandemic accelerated the transition to remote work, pushing businesses to rethink their strategies for securing remote connection. The implications of insecure connections can be detrimental, leading to data breaches, loss of sensitive information, and a damaged reputation. Therefore, understanding the risks involved and how to mitigate them is essential for maintaining a competitive edge.
Common Threats to Remote Connections
- Data Interception: Cybercriminals can intercept data transmitted over unsecured networks, leading to unauthorized access to sensitive information.
- Phishing Attacks: Employees may fall victim to cleverly disguised phishing emails that trick them into revealing login credentials.
- Malware Infiltration: Remote devices are vulnerable to malware that can compromise the entire business network.
- Weak Passwords: Many users employ easy-to-guess passwords, making it easier for attackers to exploit security weaknesses.
Best Practices for Securing Remote Connection
To effectively secure remote connection, businesses must implement a multi-layered approach to cybersecurity. Below are the best practices that should be followed:
1. Implement Multi-Factor Authentication (MFA)
Multi-factor authentication significantly enhances the security of remote access. By requiring additional verification steps—such as a text message code or a biometric scan—organizations can thwart unauthorized access attempts, even if passwords are compromised.
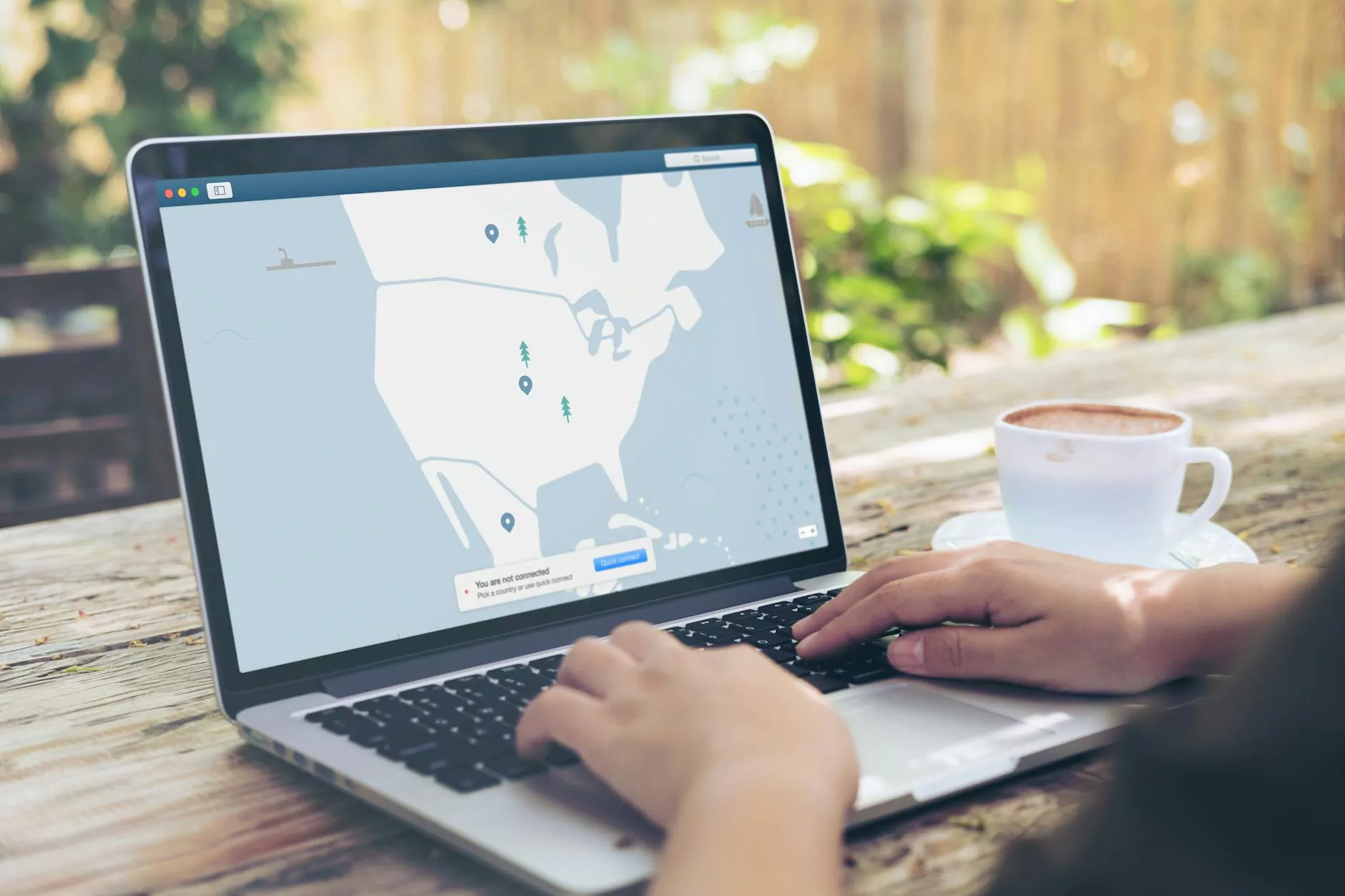
2. Use Virtual Private Networks (VPNs)
A VPN encrypts internet traffic, ensuring that data transmitted between employees and the company’s network remains secure. This is particularly important for employees working remotely over public Wi-Fi networks.
3. Regular Software Updates
Keeping all software updated reduces vulnerabilities that cybercriminals can exploit. Regularly patching operating systems, applications, and security software is essential to protect against emerging threats.
4. Educate Employees on Cybersecurity
Comprehensive training programs focused on cybersecurity can greatly reduce human error. Employees should be aware of recognizing suspicious emails, the importance of strong passwords, and safe browsing practices.
5. Secure Endpoints
Every device that connects to the company network can be a potential entry point for threats. Ensure that all endpoints, including smartphones and laptops, are protected with antivirus software, firewalls, and encryption.
Choosing the Right IT Services for Remote Security
Outsourcing your IT services & computer repair needs to a professional service provider can drastically improve your remote security posture. Here are some criteria to consider when selecting an IT service partner:
1. Experience and Expertise
Choose a service provider with a solid track record in cybersecurity. They should offer specialized knowledge in securing remote connections and experience in your industry.
2. Comprehensive Support Services
Look for IT services that provide end-to-end support, from initial risk assessment to ongoing monitoring and updates. A proactive approach will better safeguard your company’s data.
3. Customizable Solutions
Your business is unique, and so are its cybersecurity needs. Opt for providers that offer customizable solutions tailored to your specific requirements and budgets.
Software Development for Enhanced Security
In the realm of software development, security should always be a primary consideration. Here are some strategies to implement secure coding practices:
1. Integrate Security into the Development Life Cycle
Adopt a security-first approach by incorporating security measures at every stage of the development process, from planning to deployment and beyond.
2. Conduct Regular Security Audits
Regularly audit code for vulnerabilities and perform penetration testing to identify and address potential weaknesses before they can be exploited.
3. Keep Up with New Security Protocols
The tech landscape is ever-evolving, and staying informed about the latest security protocols and vulnerabilities is essential for effective software development.
Monitoring and Response Strategies for Remote Security
Even with the best preventive measures in place, incidents can still occur. Having a robust monitoring and incident response plan is vital for minimizing damage. Here’s how:
1. Real-Time Monitoring
Utilize security information and event management (SIEM) tools for real-time monitoring of network traffic and user activity to detect and respond to threats promptly.
2. Establish an Incident Response Team
Create a dedicated incident response team to handle security breaches efficiently. Regular drills can prepare them for real-world scenarios.
3. Analyze and Learn from Incidents
After an incident, conducting a thorough analysis can uncover weaknesses in your security protocols and inform future strategies for securing remote connection.
Conclusion: The Future of Remote Work Security
As remote work becomes a standard practice, the responsibility of securing remote connection will continue to grow. By implementing robust security measures, educating employees, and partnering with skilled IT service providers, businesses can safeguard their operations against the ever-present threat of cybercrime.
Take Action Now
The threat landscape is vast, but with the right approach, you can protect your business. Invest in your cybersecurity strategy today to ensure a secure remote working environment for your employees and clients alike.